In March 2022, the Payment Card Industry Security Standards Council (PCI SSC) issued the newest edition, version 4.0, of the Payment Card Industry Data Security Standard (PCI DSS). The latest revision is a modernization of the standard to address emerging threats, include new security technologies, and provide an overhaul and upgrade of the standard. PCI DSS v4.0 is also intended to allow organizations more flexibility in the methods used to meet their security goals.
In March 2022, the Payment Card Industry Security Standards Council (PCI SSC) issued the newest edition, version 4.0, of the Payment Card Industry Data Security Standard (PCI DSS). The latest revision is a modernization of the standard to address emerging threats, include new security technologies, and provide an overhaul and upgrade of the standard. PCI DSS v4.0 is also intended to allow organizations more flexibility in the methods used to meet their security goals.
What is PCI DSS?
PCI DSS is a security standard for organizations that store, process, or transmit cardholder data (CHD) and/or sensitive authentication data (SAD). Cardholder data and sensitive authentication data are defined as follows:
PCI DSS is a security standard for organizations that store, process, or transmit cardholder data (CHD) and/or sensitive authentication data (SAD). Cardholder data and sensitive authentication data are defined as follows:
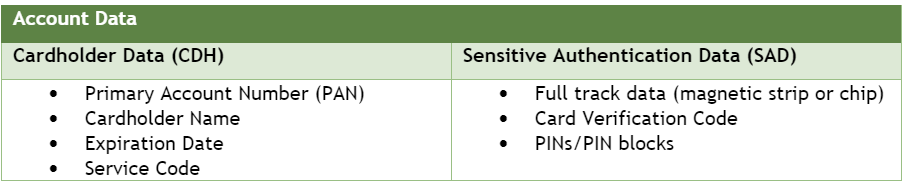 PCI DSS also applies to an organization’s cardholder data environment (CDE), particularly if they transmit an account holder’s PAN by itself or with other CDH, such as cardholder name and/or expiration date.
PCI DSS also applies to an organization’s cardholder data environment (CDE), particularly if they transmit an account holder’s PAN by itself or with other CDH, such as cardholder name and/or expiration date.
Changes to PCI DSS
Since the publication of the previous version, v3.2.1, in February 2018 the technology and environment for the payment industry has continued to evolve. The growth in payment processors, technologies, and the increasing use of cloud service providers necessitated the PCI SSC to look at ways for the standard to be more inclusive, provide clearer guidance, and provide organizations more flexibility in how they protect CDH and SAD.
The changes in the PCI DSS are classified per the PCI SSC into three specific types:
-
Evolving Requirement – Changes to ensure the standard is up to date with emerging threats and technologies, and changes in the payment industry.
-
Clarification or Guidance – Updates to wording, explanation, definition, additional guidance and/or instruction to increase understanding or provide further information or guidance on a particular topic.
-
Structure or Format – Reorganization of content, including combining, separating, and renumbering of requirements to align content.
All the changes in PCI DSS v4.0 fall into one of these three categories. The Evolving Requirement category covers the most substantial changes to the standard.
Flexibility in Implementation
PCI DSS is introducing a new method of validation known as Customized Implementation. This will allow organizations to implement security solutions that meet the specific PCI DSS objective instead of having to follow the specific methods prescribed by the standard. This will also free organizations from having to implement compensatory controls that may be a burden on their organization.
To help implement this, PCI DSS has removed “firewalls” and “routers” in Requirement 1 and replaced them with the broader term “network security controls”. This change means PCI DSS now supports a broader range of security technologies organizations can utilize to meet their security objectives.
More Stringent Access Controls
 PCI DSS v4.0 comes closer in alignment with the National Institute of Standards and Technology (NIST) guidance on digital identities and Identity and Access Management. The changes in v4.0 include:
PCI DSS v4.0 comes closer in alignment with the National Institute of Standards and Technology (NIST) guidance on digital identities and Identity and Access Management. The changes in v4.0 include:
-
Multifactor Authentication (MFA) will be required for all accounts that have access to cardholder data, not just administrators.
-
Passwords for accounts used by systems and applications:
-
Must be changed at least ever 12 months or whenever compromise is suspected.
-
Must contain at least 15 characters including alphabetic and numeric characters. These passwords must be compared against the PCI DSS list of known bad passwords.
The new standard will also allow for organizations to build their own unique, pluggable authentication solutions.
Expanding Encryption Requirements
 Encryption requirements are being expanded to include all transmission of CHD, including transmissions on trusted networks. The reason behind this change is to counter the rising threat of malware that, once on a system, can exfiltrated CDH through data transmissions.
Encryption requirements are being expanded to include all transmission of CHD, including transmissions on trusted networks. The reason behind this change is to counter the rising threat of malware that, once on a system, can exfiltrated CDH through data transmissions.
In addition, organizations will be required to implement methodologies to locate all sources and locations of cleartext PANs and the data discovery will need to be performed at least annually or upon any significant change to the CDE or processes.
Other Changes
The PCI DSS is moving towards a more ‘risk based’ framework instead of mandating the controls to be implemented. Organizations will have to evaluate their CDE through a risk assessment model and provide justifications for including, excluding, or customizing the controls they use to meet the objectives of the standard. This will help ensure organizations are taking an active role in evaluating and upgrading the security posture of their CDEs.
Security Awareness Training requirements are also being strengthened and expanded to include current threats and vulnerabilities including Phishing and Social Engineering.
Organizations will also have to document and confirm the accuracy of their PCI DSS scope annually or upon any significant changes to their CDE. For service providers, the requirement for reviewing and confirming their PCI DSS scope will be every three months or upon changes to their CDE.
Timeline for PCI DSS v4.0 Implementation
The previous version of PCI DSS (v3.2.1) will remain operational until March 2024, two years after the release of version 4.0. As of March 31, 2024, the previous version will be retired.
The two year rollout will allow organizations time to understand and implement the changes required by v4.0. Organizations will need to be compliant with v4.0 by March 31, 2025.
Sources: